Azure AD Improve App Property Lock Security
Stopping unauthorized or unintentional changes to an application’s configuration, the Azure AD App Property Lock functionality was created. Locked in place, these aspects of the application cannot be altered until they are unlocked.
Activating App Property Lock renders updates to credentials, such as the client secret or certificate, illegal. Accessing the settings requires the initial unlocking of the application.
Control over application configuration is essential for organizations wishing to maintain strict oversight, ensuring that authorized personnel can solely modify settings. While useful, this feature demands prudence because it can block authorized changes to application settings.
Why Attackers Go After OAuth Apps
A past tactic involved attackers incorporating a X.509 certificate into an enterprise app. Without monitoring audit events related to application updates, new credentials may go unnoticed and an attacker may exploit them to obtain an access token granting the app desired permissions. App permissions alone are enough for attackers to take action. Accessing the data allowed by permissions, the attackers utilize the access token instead. Mailboxes may contain accessed items, while SharePoint Online sites could hold sensitive documents at risk. After breaching the target repository, attackers may exfiltrate or delete data, which could be a case of “wiperware” used against Microsoft 365.
Not a theoretical threat, hijacking OAuth permissions assigned to applications is a reality. The SolarWinds campaign employed what in 2021? Attackers produced an X.509 certificate, which they added to Azure AD apps to access data through highly privileged programs. In September 2022, attackers leveraged an OAuth app for creating an inbound connector to spread spam.
- Access to sensitive data: Access to sensitive user data, including email addresses, contacts, calendars, or financial information, is within reach for attackers who target OAuth apps.
- Access to other applications: Credentials stolen from an OAuth app can grant unauthorized access to other OAuth-based systems and services.
- Trust: Trust is fostered when established companies like Microsoft develop OAuth apps. By attackers, user data or devices could potentially be accessed via these apps.
- Ease of exploitation: Easy exploitation is possible due to OAuth app weaknesses. If an app does not validate tokens received from OAuth providers, an attacker could potentially forge said tokens for unauthorized access.
Azure AD Improve App Property Lock Security
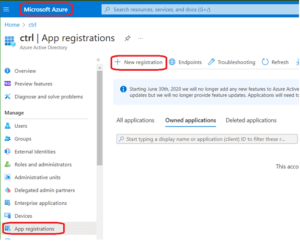
- Sign into the Azure Active Directory portal.
- Select App registrations.
- Select New Registration
Azure AD Improve App Property Lock Security
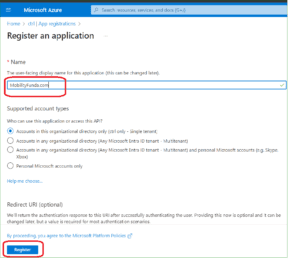
4. Add Name of the App then Select Register
Azure AD Improve App Property Lock Security
5. Under the App Registration, select Authentication, and tap on Accounts in this organizational directory only (Single tenant)
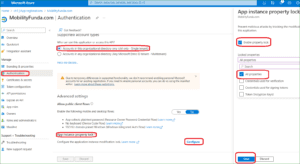
6. In App instance property lock Select Configure
7. Select “Enable property lock” section and enable the feature
Save
Azure AD Improve App Property Lock Security
Save the changes and the property lock is in force. Any subsequent attempt to update credentials will fail anywhere outside the home tenant.
Attacks Don’t Stop When a Hole Closes
Good that Microsoft is patching one of the weaknesses exploited by attackers via the Azure AD App lock. Around the protection of cloud services, an example of a chess match takes place between attackers and defenders. Now that the hole is being closed, attackers need to decide their next move. To identify questionable activity, remain vigilant while checking the audit log frequently.
Never-ending, the fight against cyber threats takes place in today’s digitized world. Evolving threats underscore the importance of safeguarding your Azure AD App Property Lock. By employing these techniques, your chances of enduring persistent assaults decrease. Leverage Azure AD’s built-in threat detection capabilities. It can identify suspicious activities and alert you in real-time, allowing for immediate response to potential threats
An ongoing commitment is safeguarding your organization’s data and reputation, remember. Be vigilant; stay informed, and stay secure.
For more information about Intune you can simply visit and understand more about What is Intune?
