Restrict Prohibited Malicious Apps with Intune
Organizations aim to dodge installing mobile apps onto devices that access corporate information after several high-profile breaches. Companies long familiar with managing endpoints via Configuration Manager quickly focus on harnessing software inventory to identify app installations.
- There will always be reasons why organizations restrict access to certain applications through their devices. On iOS and Android, Microsoft Intune Endpoint Manager enables app blocking features.
- Reactive in nature, tracking issues through inventory-based reporting is. With Intune, organizations can be proactive and establish policies.
- Mobile device inventories may not always match the actual inventory. Depending on the platform (iOS, Android, etc.), there are differences.
- Without being able to manually initiate an inventory, the issue persists that Intune cannot always offer mobile device software stock status data access. Not fully updated the results are.
Another method must be used for both operations systems. Without the option to stop installations, the iOS system relies on the Compliance Policy; post-restricted app installation, it blocks data access right away.
How can you stop the installation of an app on an Android device?
Manage restricted app on Android devices with Intune
Personal devices with work profile. Users with Intune can manage their personal accounts and work accounts, with personal accessing the public Google Play Store while work is limited to approved apps through the Managed Google Play Store. With automatic provisioning of work profiles and managed Google Play accounts through Intune, App installation happens more in personal profiles than work profiles. Customization of data sharing settings is done through device configuration profiles. Alongside Android Enterprise Configuration Profiles and apps approved for installment, BYOD work profiles may also include App Protection Policies for Android. Managed or inventoried, personal profiles cannot be.
Fully managed corporate devices. Users can install approved apps through the Managed Google Play Store or Android Enterprise Work Profile devices. With Intune, approved Android Enterprise device apps can download discreetly, plus you get the authority to remove them. Unlike work profiles, most apps found in the public Google Play Store can also be installed on managed devices. With fully managed devices, users have the choice to link their very own accounts.
Manage restricted app on iOS devices with Intune
Except through its managed services, Apple has never offered an automated means to remove iOS apps. Either Intune pushed them or installed them through the Company Portal.
1. Devices bearing prohibitive installations must have their existence reported by Intune.
2. Installing the malicious app allows us to push an uninstall command to it once.
3. Until users uninstall prohibited apps, access to corporate resources can be blocked by Azure AD Conditional Access.
A Compliance Policy needs to be in place for iOS devices, which blocks non-compliant devices from accessing corporate data. We add the Bundle ID of Facebook or any apps you want to the Compliance Policy, so as soon as a user installs the app, the device is marked as non-compliant and access to corporate data is denied or restricted.
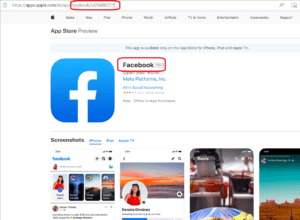
In the Apple App Store, use a browser to look up the Bundle ID of App. There is an app ID at the end of the URL. Look for the number after ID.
The Bundle ID can be found in the website URL for bundle ID, for Facebook that`s id284882215
Restrict Prohibited Malicious Apps with Intune
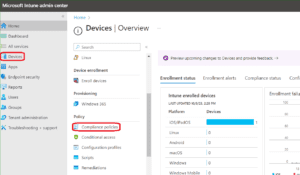
Create a Compliance Policy
Restrict Prohibited Malicious Apps with Intune
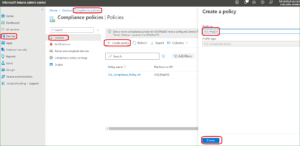
Click on Create
Restrict Prohibited Malicious Apps with Intune
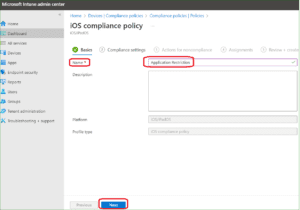
Provide name of the Compliance policy
Restrict Prohibited Malicious Apps with Intune
Select System Security and in device Security option Provide bundle ID for restricted application Name and Bundle ID
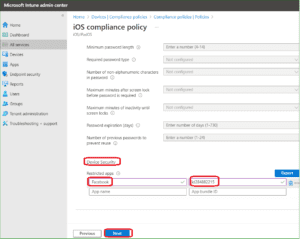
Restrict Prohibited Malicious Apps with Intune
Based one the requirement you can select the trigger option.
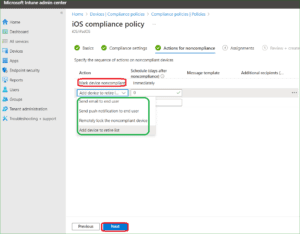
Restrict Prohibited Malicious Apps with Intune
Finally policy has been crated and you can deploy and secure your environment.
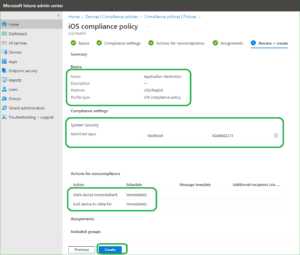
Restrict Prohibited Malicious Apps with Intune
For more information about Intune you can simply visit and understand more about What is Intune?
